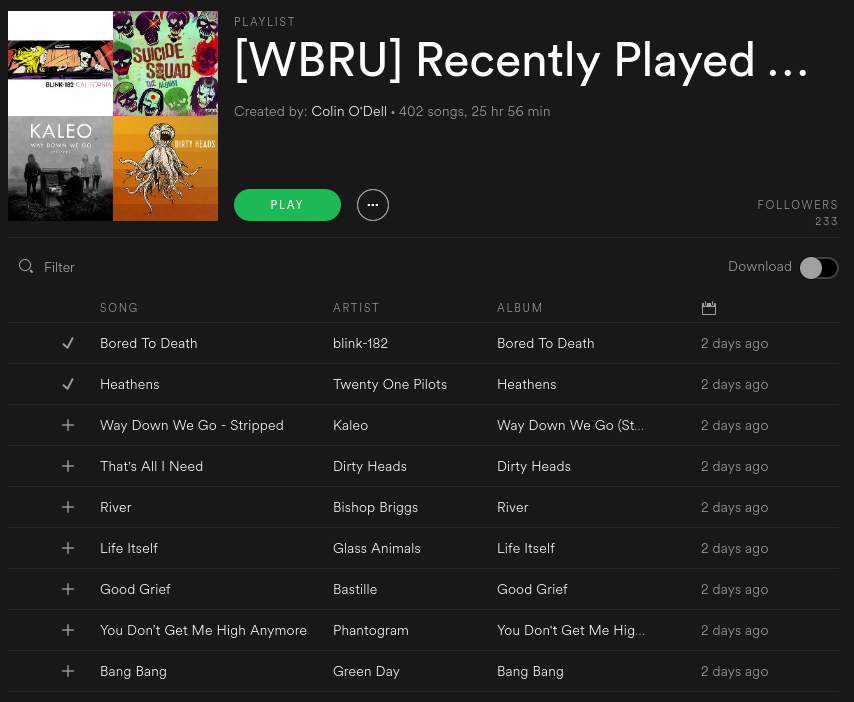
A small side-project to automatically create/update Spotify playlists with songs played by my favorite radio station (as recorded by TuneGenie).
You can listen to the auto-generated Spotify playlists here:

A small side-project to automatically create/update Spotify playlists with songs played by my favorite radio station (as recorded by TuneGenie).
You can listen to the auto-generated Spotify playlists here:
The goal of this talk is to educate developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, session hijacking, and insecure direct object references. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples.
Software bugs are inevitable; some are especially difficult to track down, causing you to waste countless hours before throwing your hands up in defeat. It doesn't have to be this way! The mental fatigue and wasted time can be avoided by using strategies like identifying the most-appropriate tool, taking a logical & objective approach, challenging assumptions, listening to variables, isolating the code path, and reinforcing code with automated tests.
This talk educates developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, and others. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples. We'll then apply this knowledge to see how web applications can be secured against such vulnerabilities.
Software bugs are inevitable; some are especially difficult to track down, causing you to waste countless hours before throwing your hands up in defeat. It doesn't have to be this way! The mental fatigue and wasted time can be avoided by using strategies like identifying the most appropriate tool, taking a logical and objective approach, challenging assumptions, listening to variables, isolating the code path, and reinforcing code with automated tests.
Firmware library for Adafruit's USB + Serial Backpack Kit with 16x2 RGB LCD.
This library only supports the TTL serial connection. Currently this library only supports the Particle Photon, though it should be possible to support other boards with minimal adjustments (if any).
Software bugs are inevitable; some are especially difficult to track down, causing you to waste countless hours before throwing your hands up in defeat. It doesn't have to be this way! The mental fatigue and wasted time can be avoided by using strategies like identifying the most-appropriate tool, taking a logical & objective approach, challenging assumptions, listening to variables, isolating the code path, and reinforcing code with automated tests.
The goal of this talk is to educate developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, session hijacking, and insecure direct object references. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples.
PHP 7 was recently released, bringing some much-desired changes and improvements to the language. However, many developers haven't had the opportunity to use it for their projects and may not be familiar with the changes it brings. We'll remedy this by checking out the new "spaceship operator," demonstrating how static type hints produce clean code, and using anonymous classes to quickly implement interfaces on the fly. Attendees will also learn about breaking changes and "gotchas" to watch out for when making the upgrade and will receive pointers on getting started with PHP 7 today.