The Internet of Things (IoT) is fundamentally changing how we interact with the digital world. In this session we’ll explore the implementation of real examples which bridge the gap between the physical and digital world using PHP: asking Alexa for information within a PHP application; displaying API data on an Arduino-powered display; using PHP to control LEDs on a Raspberry Pi to monitor application uptime; and connecting IR sensors to Slack to see whether a conference room is in use.
PHP
Software bugs are inevitable; some are especially difficult to track down, causing you to waste countless hours before throwing your hands up in defeat. It doesn't have to be this way! The mental fatigue and wasted time can be avoided by using strategies like identifying the most-appropriate tool, taking a logical & objective approach, challenging assumptions, listening to variables, isolating the code path, and reinforcing code with automated tests.
In this episode I chat with Cal Evans about PHP, Alexa skills, and ZendCon 2017!
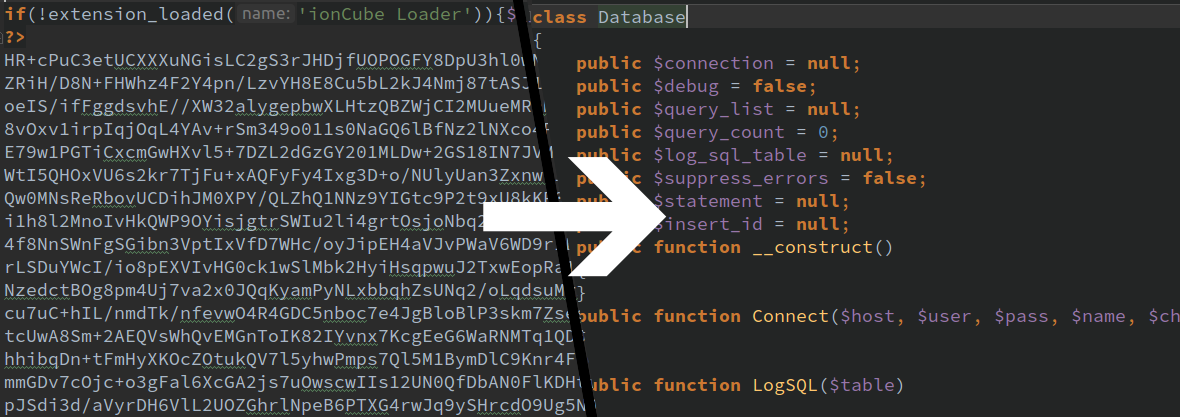
I recently inherited a legacy PHP project built on a closed-source framework where all the core classes were encrypted with IonCube. Not knowing what classes and methods exist makes it extremely difficult to use that functionality. In order to make life easier, I set out to create a stubs.php file listing all of those "hidden" classes and methods.
This morning I came into work to find my Packagist download counter had rolled over: league/commonmark now has over 1,000,000 downloads!
To celebrate this milestone I thought I'd share the story of how this package came about, how it's grown, and how I couldn't have reached this milestone without the PHP community's help.

A simple, modern PHP library to identify, convert, and enumerate IPv4 IP addresses and subnets. Forked from https://github.com/tapmodo/php-ipv4

A 7-segment display shows how many times my league/commonmark library has been downloaded by pulling data from packagist.org.
PHP 7.2 is slated for release in November 2017, but you don't have to wait until then to start testing your applications! We can easily use Docker to test against the latest pre-release versions of 7.2.
PHP 7.2 Pre-Release Images
PHP now has official pre-release Docker builds available. You should use those instead.
I recently needed the ability to perform a RIGHT JOIN in a Symfony project. While Doctrine's DBAL library seems to support this, the ORM's QueryBuilder does not. Unfortunately, the suggested workaround of inverting the query wouldn't work in my situation. I also didn't feel like rewriting the query into DQL, so I ultimately hacked in my own support by duplicating the LEFT JOIN functionality. I figured I'd share my patch in case it helps others facing a similar issue.
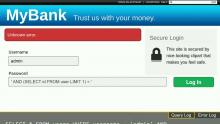
This talk educates junior and mid-level developers on common security vulnerabilities, how they are exploited, and how to protect against them. We'll explore several of the OWASP Top 10 attack vectors like SQL injection, XSS, CSRF, and others. Each topic will be approached from the perspective of an attacker to see how these vulnerabilities are detected and exploited using several realistic examples. We'll then apply this knowledge to see how web applications can be secured against such vulnerabilities.